NGINX Modern Apps > Class 11 - F5 NGINX Plus Ingress Controller as an API Gateway for Kubernetes > Task 06: API Request Rate-Limiting Source | Edit on
Task 06: API Request Rate-Limiting¶
In order to ensure fair use of our API, we need to protect against a single user crowding out other users.
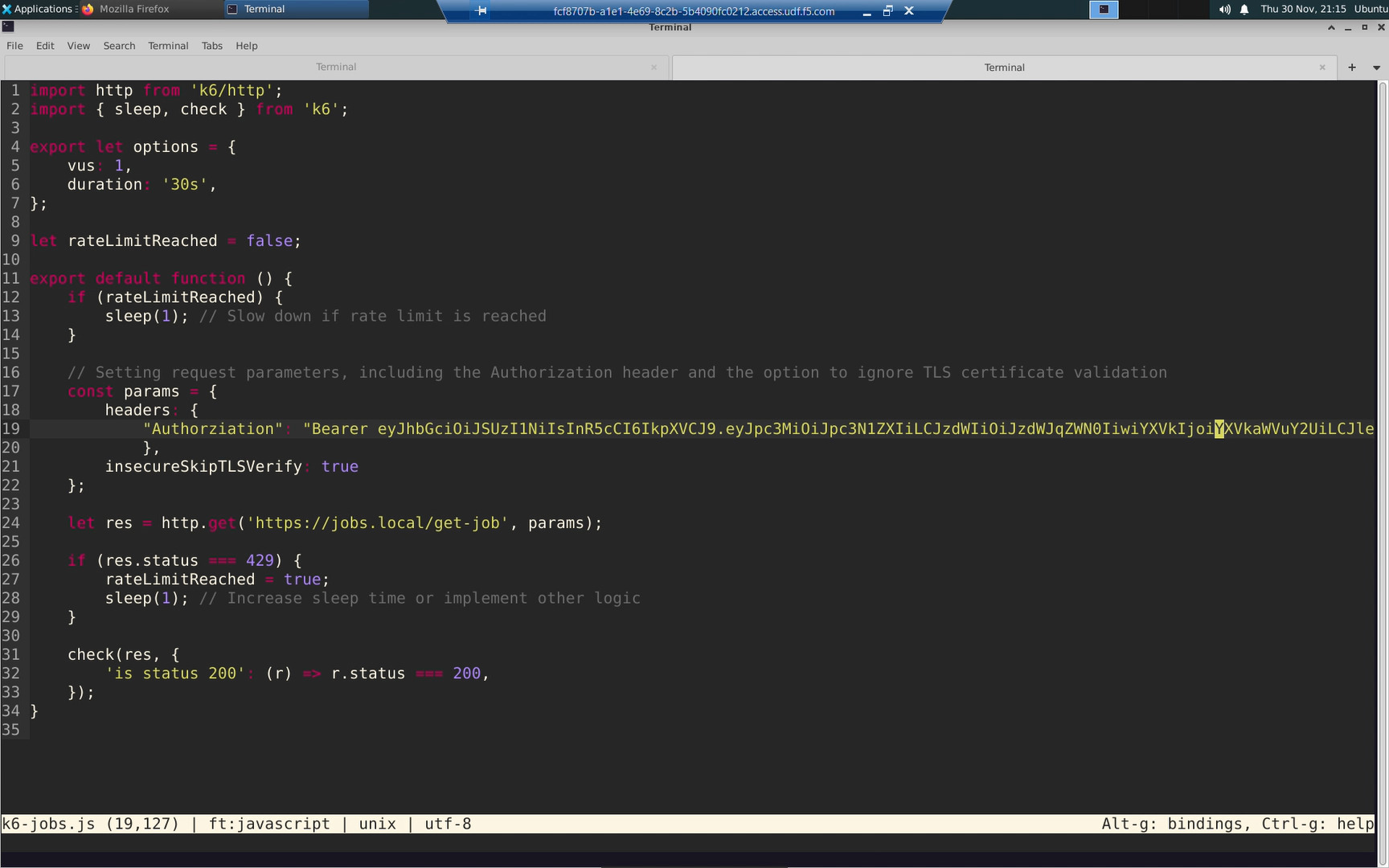
NGINX Plus can rate-limit the API requests of a single user. The rate-limit policy can be keyed to their “Authorization” header.
Open a new terminal tab. We will run an HTTP load test from the jumphost to the https://jobs.local/get-job API endpoint to confirm the rate-limit policy is working.
The reponse should be: jumphost.
You should now have two terminal tabs open:
- [Tab #1] microk8s1
- [Tab #2] jumphost
From jumphost, download the load test script.
From microk8s1, lookup your JWT token.
From jumphost, edit the HTTP load test script to include your JWT token in every request.
If you are unfamiliar with the micro text editor:
- Ctrl + V [Win] or Cmd + V [Mac] to Paste
- Ctrl + S [Win] or Cmd + S [Mac] to Save
- Ctrl + Q [Win] or Cmd + Q [Mac] to Quit/Exit
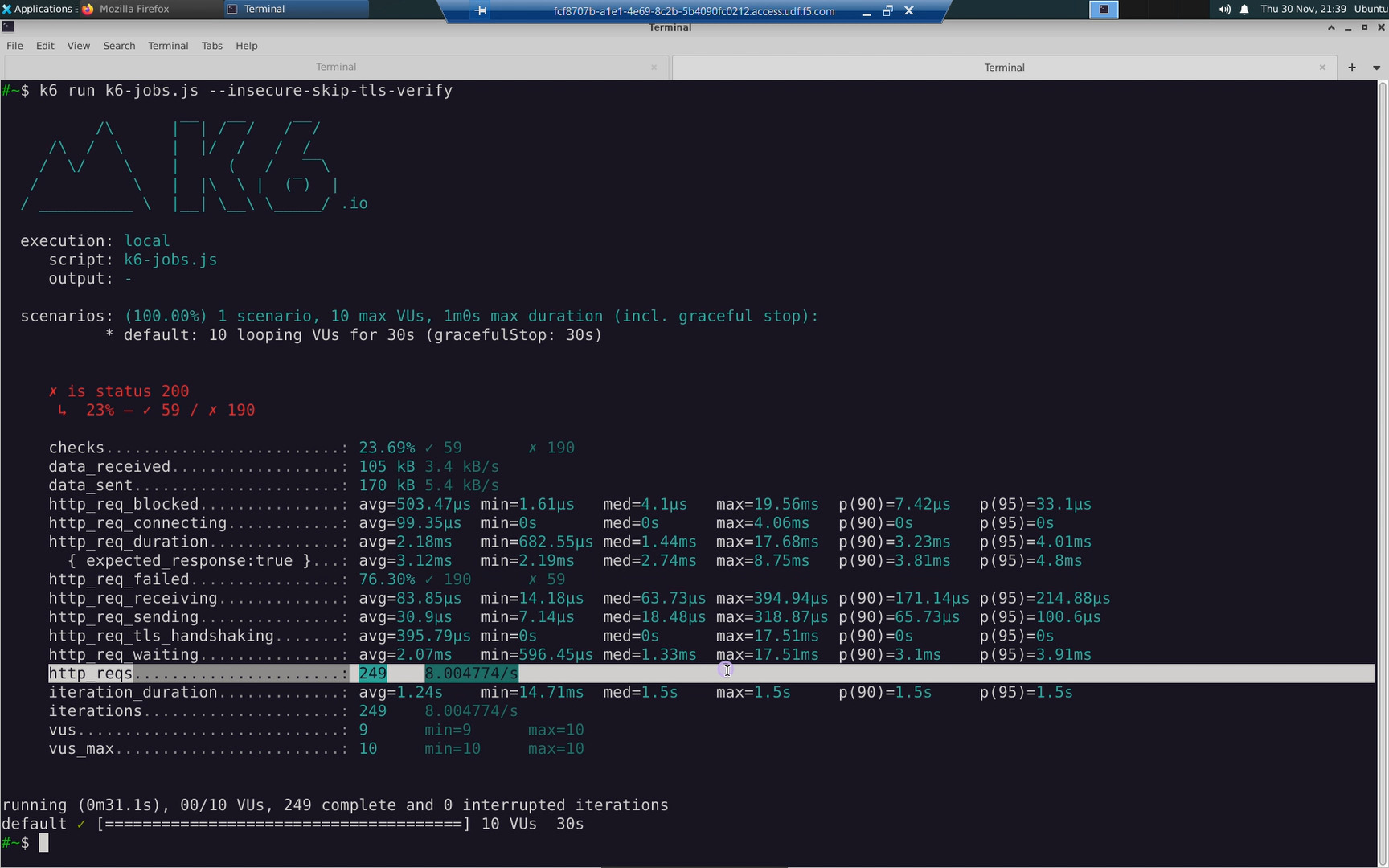
From jumphost, run the http request load test.
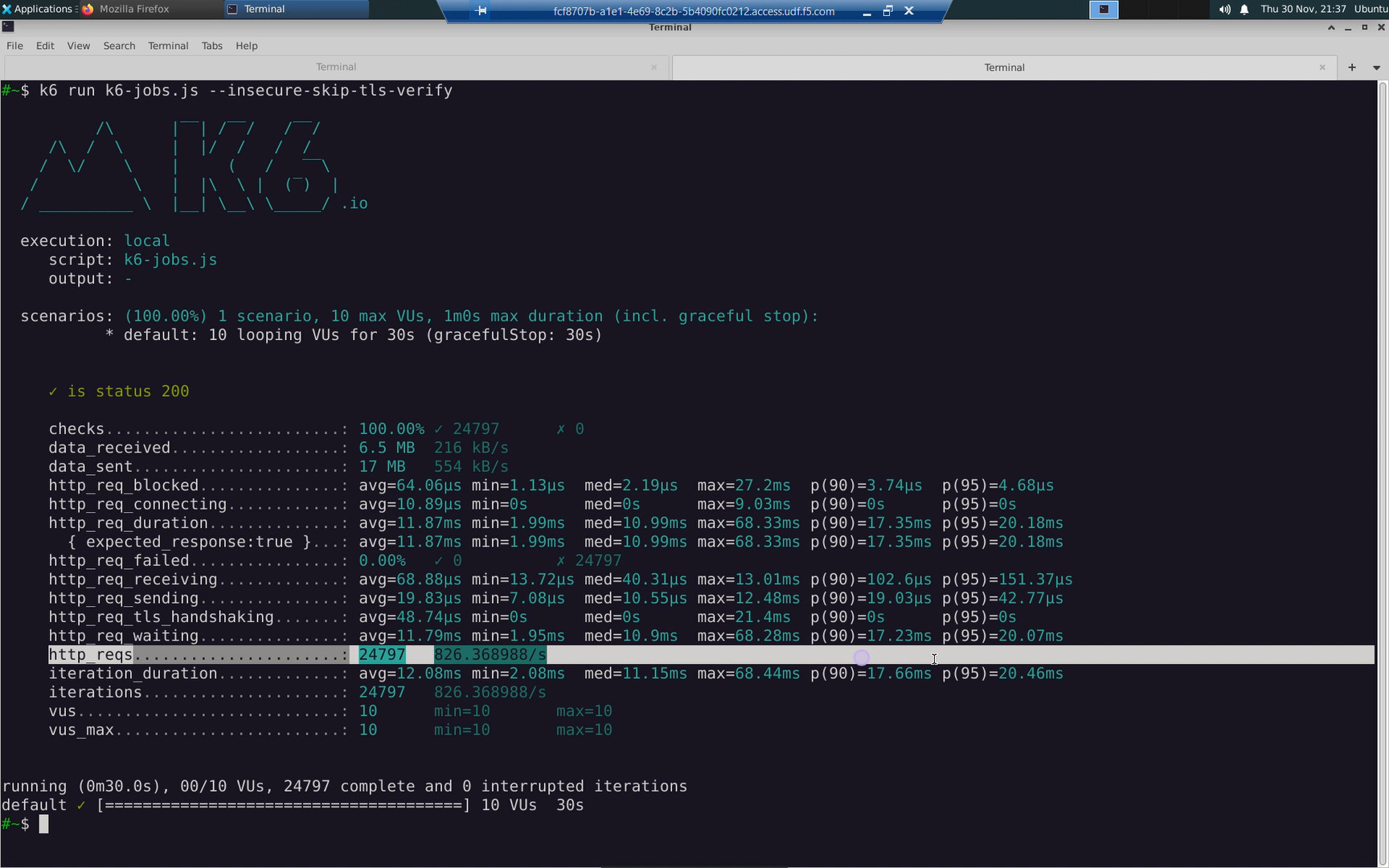
Note the row reporting http_reqs. These are the successfull HTTP requests made by the client.
From microk8s1, change to the task_06 directory.
Create a rate-limit policy. Our rate-limit policy will limit clients to 10 HTTP requests-per-second keyed to the Authorization HTTP header. You can key the rate-limit policy to client IP address, any arbitrary HTTP header, and more.
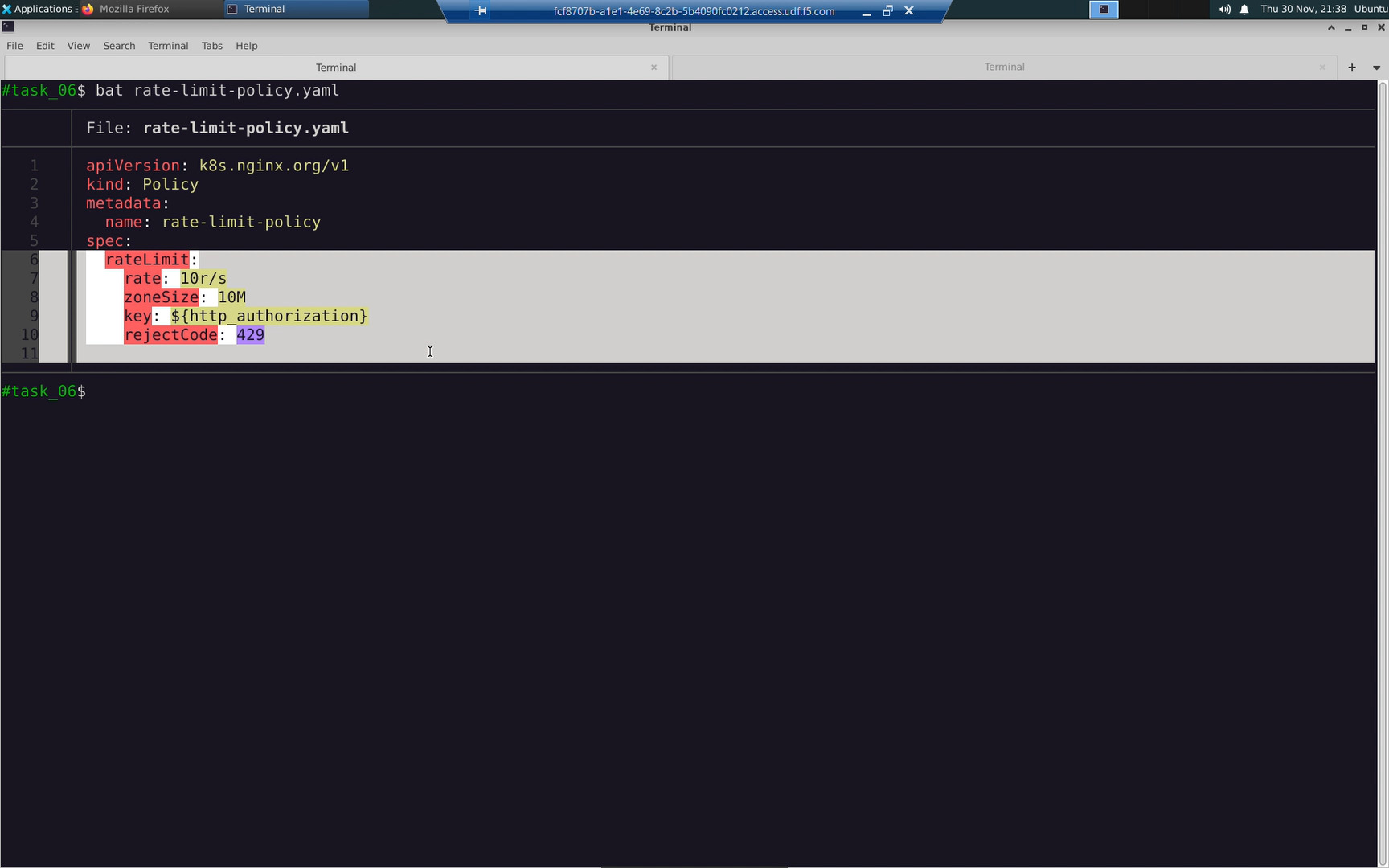
| rateLimit | ||
|---|---|---|
| Property Name | Value | Comments |
| rate | 10r/s | 10 requests per second |
| zoneSize | 10M | 10 MegaBytes |
| key | ${http_authorization} | HTTP Authorization Header |
| rejectCode | 429 | Too Many Requests |
Modify my-virtualserver to reference the rate-limit policy. This has already been prepared for you in the lab.
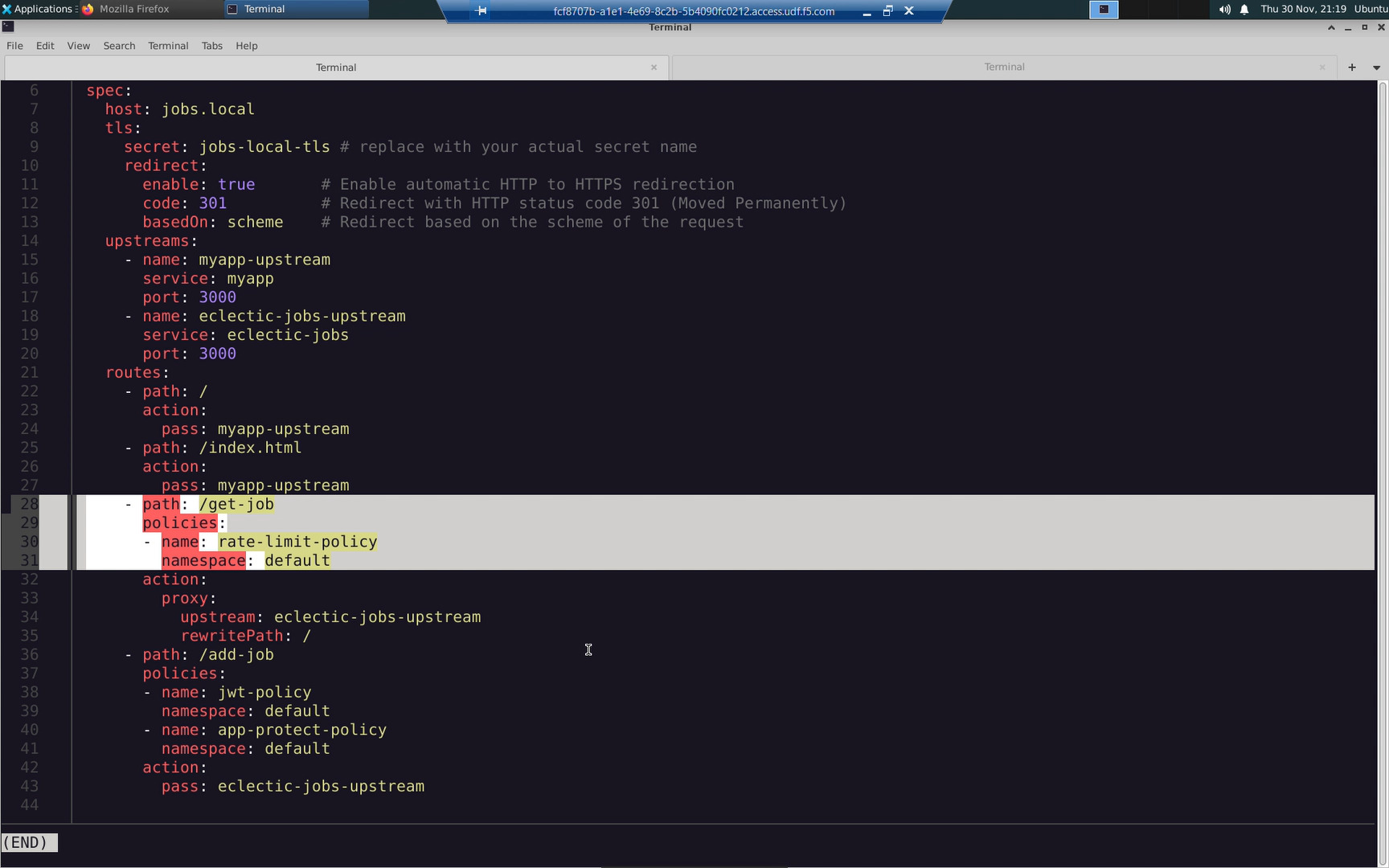
Confirm the status of the virtualserver ‘my-virtualserver’ you just modified.
From jumphost, run the same HTTP request load test again now that a rate-limiting policy has been applied. When the client exceeds the requests per second specified in the rate-limit policy, it will receive a 429 “Too Many Requests” error. Our client is configured to be well behaved and will slow down the rate of requests. Note the http_reqs recorded under the rate-limit policy will be roughly ~10/s.