F5 BIG-IP SSL Orchestrator Training Lab > All SSL Orchestrator Lab Guides > SSLO 101: Essential SSL Visibility with SSL Orchestrator (Agility 2022 | 2 hours) > 3. Create a Transparent Forward Proxy SSLO Source | Edit on
3.14. Review behavior prior to decryption¶
This test will demonstrate that:
Traffic is not being decrypted
The "malicious" file will pass through the network-based scanner and be download to the client.
3.14.1. RDP to the Client machine¶
From UDF, find the Ubuntu18.04 Client.
Click Access.
Under xRDP, choose your preferred resolution.
At the Login to xrdp window, click on the OK button.
You will then see the Client desktop.

3.14.2. Server certificate test¶
Open Chromium web browser on the outbound client system and navigate to any remote HTTPS site (e.g., https://www.google.com). Once the site opens in the browser, click the padlock to the left of the URL.
Click Certificate (Valid).
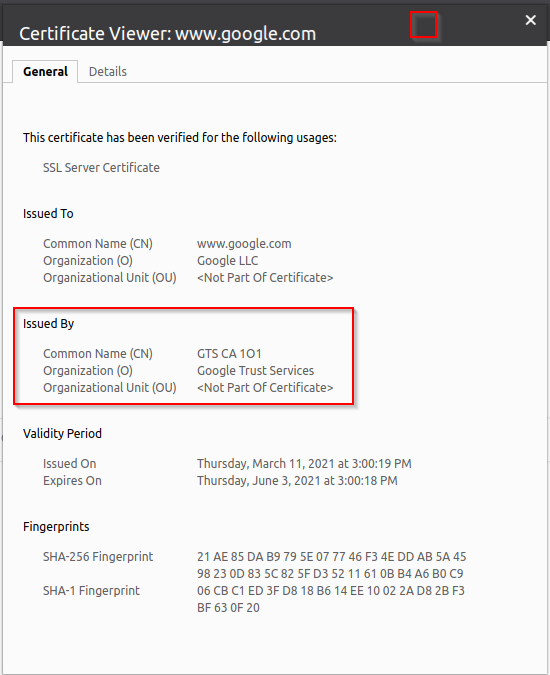
Review the server certificate of the site and notice that it is signed by a public certificate authority (CA).
This confirms that the certificate re-write and SSL forward proxy decryption functionality provided by SSL Orchestrator is currently disabled.
3.14.3. Encrypted traffic test on the security service¶
Open Chromium web browser on the outbound client system and navigate to https://eicar.org/?page_id=3950. Scroll down to the section labeled Download area using the secure, SSL enabled protocol HTTPS and click on eicar.com. This is a non-malicious file that antivirus products will detect for testing purposes.
Notice that the encrypted malware test file is scanned by CLAM_AV and downloaded to the client without issue.
In the next section, you will perform the same test after enabling decryption.